Cloud computing is quite a buzzword in the paradigm of technology. It approximately appears 48 millions of times on the Internet search engine results. It has been in the popular tech lexicon for over a decade and yet only a handful of people get the concept of cloud computing. I have provided a detailed analysis of what Cloud computing exactly is and how to secure data in this blog.
‘Why do I need to worry about cloud computing?’ If you have this thought in your mind right now, let me tell you cloud computing is the future of everything. From the data centre to the mobile phone, cloud computing will transform the digital world beyond your imagination. Gear yourself up because I am going to clear the air regarding cloud computing.
What Exactly Is Cloud Computing?
Cloud computing is the delivery of computing infrastructure, platforms, services and applications from the Cloud to the users through the Internet. Is it too much of technical jargon to take in? Here is a simple example that you can relate to. It is similar to renting an apartment instead of buying your own home. You pay a monthly rent for maintenance and the landlord takes care of your belongings in return.
Cloud computing technology can be classified into three different categories. Have a look at the basics of cloud computing to understand how different types of cloud computing work. Here is an overview of the 3 different cloud computing technologies.
-
Platform as a service (PaaS)
It provides a cloud platform through which you can develop, run and manage applications without having to maintain the infrastructure.
-
Infrastructure as a service
It provides computer resources such as networking, storage, servers and data centre space. You have to pay on a monthly or yearly basis to avail these services.
-
Software as a service
This one is run on distant computers owned by someone else. You can connect with the user’s computer via the Internet and a web browser.
Each of these services has some remarkable benefits of their own. You may wonder what would happen to the data you store on Cloud. Will it be safe? What if I lose data without any backup? I too had similar questions when I kicked off my career in this field for the first time. Here are some easy steps to secure your data in the Cloud.
Steps To Secure Your Data In Cloud [H2]
As per Gartner, the number of Cloud users increase every day. It is an ideal place for businessmen to exchange projects and assignments with ease from allessaywriter. Despite advanced Cloud technology, the risk of losing data in Cloud has increased considerably. Check out these simple methods to secure data in the Cloud.
-
Keep a local backup, no matter what
It is the simplest method that you can execute to keep your data safe in the Cloud. You may not have control over the misuse of data on the Internet. But, you can always save your data from getting lost. The IT world mostly works on these data and losing files can lead to financial loss. You may be confused with plenty of cloud backup services out there. Toms Guide, a renowned tech-based blog, has narrowed down the list and it can help you choose the best service for your organisation.
-
Use encrypted data
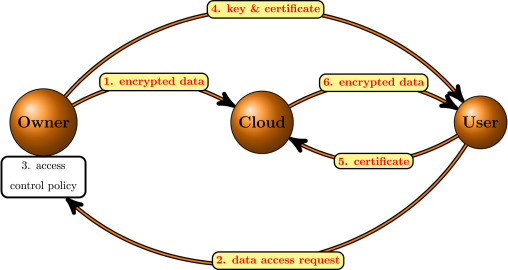
I always suggest my followers to encrypt the data before uploading it to the Cloud. This is a great step in preventing your data from being attacked by hackers. Local encryption makes use of zero-knowledge proof to protect your data against different administrators and service providers. Before choosing your cloud service provider, make sure it provides data encryption. People who already use an encrypted cloud service should have a preliminary round of encryption to walk that extra mile to secure the files.
-
Do not save sensitive information
Most organisation prefer to store sensitive information in the Cloud. Sensitive data might be safe as long as it is in the Cloud. What happens when the information leaves the Cloud or when you share it with someone? Data breaching is common these days and you can avoid it by not storing sensitive data in the Cloud. Leading industries such as Facebook have also been dragged to court due to the sharing of sensitive information. Keeping all the consequences in mind, my advice is to keep sensitive information away from the Cloud.
-
Use strong & reliable passwords

Gone are the days when you could use your favourite colour or your best friend’s name in the password. You need to use discretion and make your passwords unpredictable. 81% of companies suffer data breaches due to weak passwords. Therefore, a strong password isn’t enough. You need to add a two-step verification process to introduce an extra level of security. In that case, you will know there is an alternative security step to take care of your data even if the first one goes amiss.
-
Use password managers
Password managers let you use all the passwords behind one master password. You will have several logins for accounts such as Facebook, Twitter and Cloud storage. The fun part is that you can login to these websites using a single password. I believe this is quite a simple way to secure data and is also a boon for people who keep forgetting their passwords. You will find several online password management utilities. Just go through them to choose the best one for your marketing service.
-
Invest in security measures
Passwords are okay. But, they aren’t enough (as I have already mentioned). You need to apply additional security measures to keep things under control. Remember that encryption prevents your data from unauthorised use, but it does not secure the existence of your data. Secure your Cloud with reliable antivirus programs, admin controls, etc. to add an extra layer of protection to your data. It is very important for the cloud system and its servers to use the right security tools that can restraint data breaches.
-
Test your security
Examining Cloud to see the quality of its performance can make all the difference between weak and strong security measures. You can also hire ethical hackers with ceh ethical hacking certification and make them check your system’s security. This way, you can also identify the possible loopholes in your security system and take appropriate actions to cover them. Cloud data requires CONSTANT attention. You can’t just assume that your data in the Cloud is safe. You need to take actions to make safeguard your data.
Wrapping it up
If you want to make the most of the Cloud, you have to define the level of protection that you will need to safeguard your information. Whether you are using two-step verification for your data security or signing up for Cloud, make sure you are ready for it. After all, paying for Cloud services isn’t a cup of tea. However, you can at least go to sleep peacefully without having nightmares about data breaches. Maintain a striking balance between the protection level that you need and the time/effort/money you are willing to spend on it.
Author Bio:
Bella Jonas is an enthusiastic tech blogger from New York, United States. Apart from being a blogger and a complete gadget freak, Bella is dedicatedly associated with allessaywriter as an essay writer for the last five years. During her time of leisure, you will find her working on amazing wall arts and creative sketches.








