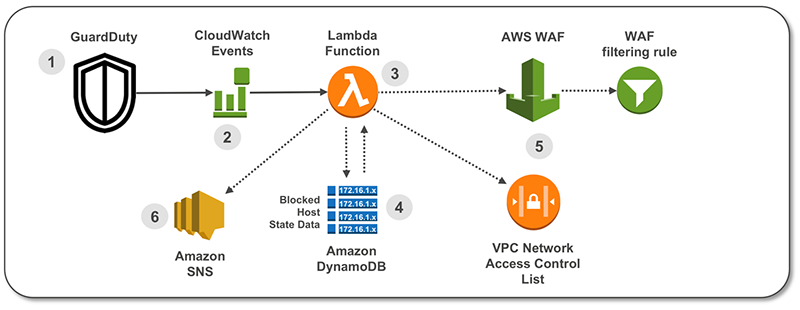
The complexity and volume of cyber threats are increasing at an unprecedented rate. Entities face relentless attacks from a slew of threats, including malware, phishing, APTs, and sophisticated intrusion attempts. Traditional security measures often fall short of providing the comprehensive, real-time protection needed to protect confidential data and critical infrastructure. This is where advanced threat detection tools like Amazon GuardDuty are becoming indispensable. By continuously monitoring for malicious or unauthorized behavior across AWS accounts and workloads, GuardDuty brings a proactive approach to identifying and mitigating threats before they can become a major problem and cause significant damage.
Moreover, modern business environments are highly interconnected, which means that a single vulnerability can have far-reaching repercussions. With the integration of cloud services and global operations, businesses need robust security solutions that can scale up and down as needed. Forward-thinking firms are turning to tools like Amazon GuardDuty to protect themselves.
GuardDuty is a managed threat detection service that continuously monitors for malicious or unauthorized behavior to help protect AWS accounts and workloads. By analyzing a variety of logs, including Amazon Virtual Private Cloud (VPC) Flow Logs, AWS CloudTrail, and DNS logs, GuardDuty provides detailed findings for visibility and remediation. It also leverages machine learning (ML) and threat intelligence to detect anomalous behaviors and provides detailed insights and automated remediation options. This helps entities respond quickly to potential threats and safeguard the integrity and security of their digital assets.
This blog will analyze three real-world scenarios where GuardDuty successfully detected and helped mitigate security incidents.
AWS Loft Event: Immediate Threat Detection and Remediation
During an AWS Loft event, a customer enabled GuardDuty in their AWS account as part of a lab exercise. Shortly after activation, GuardDuty detected multiple Amazon Elastic Compute Cloud (EC2) instances communicating with known command and control servers. This was a sure sign that the EC2 instances had been compromised and were being used as part of a botnet.
Insights and Lessons Learned
- Immediate Action on Findings: The detection led to a swift investigation by the customer’s security team, highlighting the importance of immediate action upon receiving GuardDuty alerts.
- Preparedness for Real Threats: Enabling GuardDuty can reveal real security issues even in a lab environment. This emphasizes the importance of routine security checks and being prepared for genuine threats.
- Continuous Monitoring: GuardDuty’s ability to provide continuous monitoring and real-time alerts is crucial for identifying and mitigating threats as they arise.
Best Practices
- Enable GuardDuty in All Accounts: Ensure GuardDuty is enabled across all AWS accounts to continuously monitor for malicious activities.
- Immediate Investigation: Always investigate GuardDuty findings promptly to understand the scope and impact of the threat.
Wix: Using GuardDuty Enhanced Protection
Wix, a web development business, integrated Amazon GuardDuty with Orca Security to improve its security posture. GuardDuty detected brute force attempts on an Amazon EC2 instance, and Orca Security provided additional context, highlighting the asset’s exposure and potential lateral movement risk.
Insights and Lessons Learned
- Enhanced Visibility and Context: Combining GuardDuty with Orca Security enabled Wix to gain deeper insights into its security alerts, improving its ability to prioritize and respond to threats.
- Reducing Alert Fatigue: By using Orca to correlate and enrich GuardDuty findings, Wix reduced the number of alerts and focused on the most critical ones, cutting alert fatigue right down.
- Comprehensive Security Coverage: The integration provided full-stack security visibility, covering all assets without gaps, ensuring a more secure environment.
Best Practices
- Integrate with Complementary Tools: Enhance GuardDuty’s effectiveness by integrating it with tools like Orca Security for additional context and prioritization.
- Focus on Critical Alerts: Use additional context from integrated tools to prioritize alerts, ensuring that the most significant threats are addressed promptly.
Dome9: Automating Remediation with GuardDuty and CloudBots
Dome9, a solution for public cloud platforms, integrated GuardDuty with its CloudBots to automate the remediation of security findings. GuardDuty findings were sent to an Amazon Simple Notification Service (SNS) topic, triggering predefined remediation actions through CloudBots.
Insights and Lessons Learned
- Automated Remediation: Automating responses to GuardDuty findings significantly reduces the time it takes to resolve security events, ensuring faster threat mitigation.
- Detailed Security Context: Dome9’s Entity Explorer provided detailed security context for each affected resource, enabling precise and effective remediation actions.
- Proactive Incident Response: With CloudBots, Dome9 customers could proactively manage security incidents, preventing further compromise.
Best Practices
- Implement Automated Remediation: Use tools like Dome9 CloudBots to automate responses to GuardDuty findings, reducing manual intervention and response times.
- Leverage Detailed Security Context: Ensure your security tools provide detailed context for each alert, facilitating accurate and effective remediation.
Mitigating Incidents in Real Time
Amazon GuardDuty’s ability to detect and mitigate security incidents in real time is invaluable for maintaining the security of AWS environments. The scenarios at AWS Loft, Wix, and Dome9 demonstrate the effectiveness of GuardDuty when it comes to identifying and responding to threats before they have a chance to impact the organization.
For cybersecurity practitioners, these examples highlight the importance of continuous monitoring, integrating complementary security tools, and automating remediation processes. By following these best practices, entities across the board can enhance their security posture and ensure a more resilient AWS infrastructure.
These real-world scenarios have highlighted how to leverage Amazon GuardDuty effectively and leave behind the key lessons of how immediate action, enhanced visibility, reducing alert fatigue, and automating remediation are crucial for maintaining robust security in complex cloud environments.
About the author:
Kirsten Doyle has been in the technology journalism and editing space for nearly 24 years, during which time she has developed a great love for all aspects of technology, as well as words themselves. Her experience spans B2B tech, with a lot of focus on cybersecurity, cloud, enterprise, digital transformation, and data centre. Her specialties are in news, thought leadership, features, white papers, and PR writing, and she is an experienced editor for both print and online publications. She is also a regular writer at Bora.